Google Registry’s recent announcement of their new top-level domains (TLDs) has attracted attention from security enthusiasts. The new TLDs include .dad, .esq, .foo, .mov, .nexus, .phd, .prof, and .zip. The .zip and .mov domains in particular have sparked debate in the security community due to their association with widely recognized file types. The key concern with these domains revolves around automatic hyperlinking.
Automatic hyperlinking
Automatic hyperlinking is where a program automatically converts text such as example.com into a clickable link like example.com. Many programs perform automatic hyperlinking including Microsoft Teams and Outlook, both of which are very common in workplaces worldwide. This means that when someone sends a message referring to a zip file it will automatically be converted to a clickable link. A hacker can easily exploit this vulnerability by purchasing a single domain that corresponds to a commonly used business term, like accounts.zip, enabling them to target numerous individuals with minimal effort.
accounts.zip
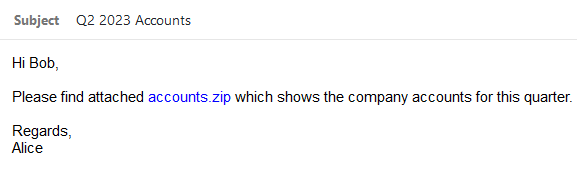
For example, imagine a scenario where Alice sends Bob the above email. This is not a phishing email and is a genuine email sent by Alice containing an attachment named accounts.zip. When Bob opens the email he notices that “accounts.zip” is in blue. He clicks it thinking it will download the attachment for him. However, instead it takes him to a page owned by a hacker called Mallory who purchased the domain accounts.zip.

Bob is presented with a page that has a message like this, since Bob trusts Alice and is expecting the email he clicks download. Mallory has now successfully lured Bob into unknowingly downloading her malware without any direct interaction with either user.
Considering the term “accounts” is widely used in businesses, Mallory can effortlessly deceive numerous victims with just one domain and minimal groundwork. This exploit is particularly dangerous as it is perpetrated unknowingly by a trusted party.
The simplest way to mitigate the risks created by these domains is to block them on all of your devices. This can easily be done by adding a wildcard domain entry to your Pi-Hole blocklist.
Do you have any opinions on .zip and .mov domains? Comment them below! (Name, Email and website are optional)